In previous posts on this blog, we have described the use of proxy forces to impose costs on a shared adversary (AKA, unconventional warfare). But perhaps the most difficult aspect of unconventional warfare is not in its planning or execution, but in knowing when it is an appropriate approach at all. A recent article from
IW Foundations
The Imperative: Irregular Warfare and the Future of Security
Irregular Challenges are at the future of international security This blog was started not just out of a personal passion for the subject matter, but a firmly held belief that the United States will increasingly be confronted by irregular challenges, and that it has a troublesome tendency to bury its head in the sand about
The Core Activities of Irregular Warfare
As discussed briefly in the previous post, current US military doctrine describes irregular warfare as having five core activities: counterterrorism (CT), unconventional warfare (UW), foreign internal defense (FID), counterinsurgency (COIN), and stability operations (SO). Rather than being viewed as a list of discrete options, these activities (sometimes called the “five pillars of irregular warfare”), according
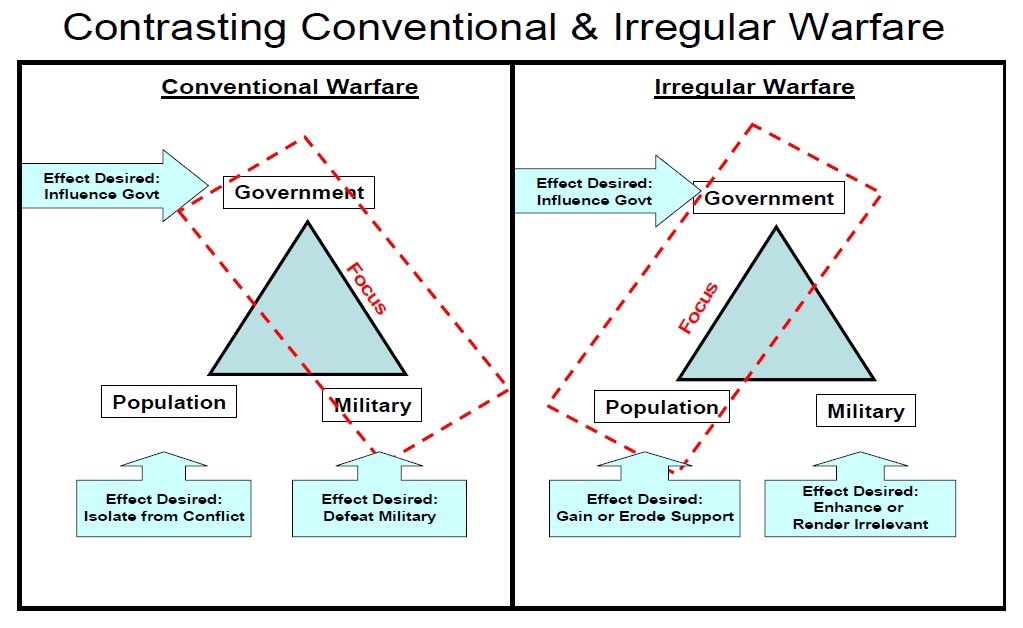
Defining Irregular Warfare
“IW is a complex, ‘messy,’ and ambiguous social phenomenon that does not lend itself to clean, neat, concise, or precise definition.”Irregular Warfare Joint Operating Concept, 2008 The above quote reflects the discomfort that the US military had (and continues to have) in coming to terms with an aspect of warfare that was becoming increasingly apparent