As discussed briefly in the previous post, current US military doctrine describes irregular warfare as having five core activities: counterterrorism (CT), unconventional warfare (UW), foreign internal defense (FID), counterinsurgency (COIN), and stability operations (SO). Rather than being viewed as a list of discrete options, these activities (sometimes called the “five pillars of irregular warfare”), according to IW JOC 2.0, may be undertaken in sequence, in parallel, or in blended form as part of a campaign to address irregular threats. It is interesting to note that of these five activities, only one–unconventional warfare–is “offensive” in a strategic sense (counterterrorism is often offensive at the operational and tactical levels, but is reactive and defensive at the strategic level). Nonetheless, there is a significant convergence between several of these activities. For example, it will often be difficult to determine if an activity in a complex operation is in support of a foreign internal defense, counterinsurgency, or stability operations line of effort. In fact, the activity may support all of these simultaneously.
Each of the core activities of irregular warfare has at least one natural partner: unconventional warfare is combatted through counterinsurgency and foreign internal defense, while counterterrorism is naturally paired with terrorism. But terrorism is not on the list according to US joint doctrine… And what about insurgency itself? The key to understanding this is realizing that the US only identified the core activities of irregular warfare according to a purely US-centric point of view. Based on the conclusion that the US does not participate in terrorism, counterterrorism is a sufficient activity to cover this domain of warfare, and the fact that insurgencies will be conducted only by proxy allow the US to focus only on unconventional warfare.
This blog takes a slightly different view of the number and organization of the core activities of irregular warfare.
First, the use of the term “pillars” is misleading as to the nature of these activities within irregular warfare doctrine. Pillars support a structure and (assuming that they are not merely cosmetic) are necessary to the integrity of that structure. However, the activities listed above are not in the abstract necessary to an irregular warfare campaign. For example, a state conducting an internal counterinsurgency may or may not require a foreign internal defense effort, while a counterterrorism campaign may find that the terrorists have no popular support, obviating the need for counterinsurgency. In the aftermath of a natural disaster, stability operations may be required to quell rioting and limit looting, but there may be no effective organization to the unrest, limiting the role of counterinsurgency to measures that are essentially prophylactic. Additionally, as the only offensive activity among those listed, unconventional warfare will in many cases be conducted in the absence any of the others.
The term “core activities” is therefore preferable to “pillars,” since it makes clear the importance of these activities in irregular warfare writ large, but does not imply that each of the activities will be necessary in every irregular warfare campaign. It also carries the implication that these activities will be the primary effort in a campaign, supported by other activities like strategic communications, psychological operations, and civil-military operations.
Beyond simple terminology preferences, there is also the more important issue of precisely what activities are core to irregular warfare. Since this blog is not specifically focused on development of US military forces (as the Joint Operating Concepts on Irregular Warfare are), this blog takes the position that there are several sets of core activities: Insurgency and Counterinsurgency; Unconventional Warfare and Foreign Internal Defense; Stability Operations; and Terrorism and Counterterrorism. In addition to regrouping the activities, it should be noted that two new activities are added: insurgency and terrorism. This is not merely an academic choice, however, since including all fundamental operational activities is essential to the study of the enemy’s strategic, operational, and tactical considerations. While it is unlikely that US forces will conduct these activities itself, it must still understand them in order to confront them (through COIN, FID and CT) and, in the case of insurgency, to support it when required through unconventional warfare. Thus, as part of a coherent classification system of irregular warfare, they must be included along with their “counter” activities.
And as has been clear from the time of Sun Tzu, understanding your adversaries’ options and strategies is a foundational requirement to confronting that adversary. This is true in any confrontational pursuit, whether it be politics, the courtroom, business, or the battlefield. In an irregular struggle, whether against a state or non-state adversary, understanding that adversary’s strategic goals, options and constraints will allow a strategist to formulate a plan to take advantage of his weakest points and properly prepare for attacks against his own. In a counterinsurgency campaign, for example, the counterinsurgent must do more that simply track down and kill the insurgent leadership, or infiltrate and destroy their sanctuary. They must also confront the political ideology driving the insurgents and their supporters in order to isolate them and transform their support structures from assets into liabilities. In order to do this, the counterinsurgent must have a keen understanding of the purposes and functions of insurgent movements and their organizational structures.
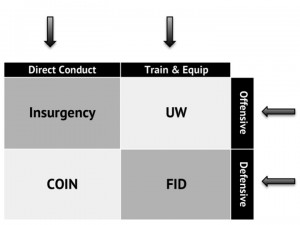
These activities are grouped into the pairs above to highlight the offensive and defensive forms of each activity. Unfortunately, as the above graphic makes clear, there is more than one obvious way that activities related to insurgency may be grouped: along offensive versus defensive lines, train and equip versus direct conduct lines, or simply as a foursome. There is no right answer, and in different discussions, it may be more useful to use one grouping rather than another. However, for most of the discussions we will pursue in this blog, the offensive versus defensive lines will be most useful, since it will help to clarify the most vital aspects of each. However, we may from time to time use alternate groupings to discuss various aspects of these activities. And the same will be true to a lesser extent for the terrorism and stability activities, as we discuss the various overlaps and blended responses inherent in confronting to irregular threats.
While each of these fundamental areas of irregular warfare are inextricably linked to one another, this blog will take on each pairing separately in a series of posts for the sake of clarity, and outline the interlinkages in the course of discussion. In addition, we will discuss other operational activity sets related to irregular warfare, such as intelligence and counterintelligence, organized crime and law enforcement, and security sector reform and assistance.
4 thoughts on “The Core Activities of Irregular Warfare”